AI, Digital Identity & Guardianship Systems?
Below are two articles i wrote and published onto linkedin, the links are below.
- https://www.linkedin.com/pulse/ai-digital-identity-guardianship-systems-timothy-holborn/
- https://www.linkedin.com/pulse/chat-gpt-most-useful-tool-accessibly-available-solve-social-holborn/
The importance of this topic, for the development of the ecosystem designs, is very high.
Below is a copy of both articles - one after the other...
As i'm working through the design process to form what i hope to become a useful technology ecosystem, i'm stuck on a problem that - doesn't matter too much for my purposes now; but if the concept develops, it'll be important to have a solution thought out ahead of time; and more broadly, with respect to society at large - I would have thought it was important for others to consider, irraspective of whether or not my works become usefully deployable.
That problem is - how to attend to the needs of persons who have some sort of guardianship related requirements. Persons who are not independently, legally capable of making their own decisions. How do you define an Authentication, Information management and Artificial Intelligence related permissions framework that best supports the needs of the person subject to some sort of guardianship related permissions system?
In my designs for an ecosystem that i've called Webizen, it is intended that in-future Adults go and buy a computing box, broadly called a Webizen. This connects to an online service that enables them to host and manage their own information and use apps that work in a way that means that they store their own information. The box, is like a digital vault, that connects to a persons devices and acts as a sort of web-server for their own personal information; enabling them to have their own AI agent (the webizen) that is defined by them to act in their interests; and support their needs in daily life. It provides an alternative to digital identity wallets, whilst offering the ability to support their means to retain copies of important documents, whether that be digital receipts; or their own copy of a call that the other party is recording.
It provides an ability to use ChatGPT like service, but privately; and it supports the means for the Webizen Owner to support their own 'smart home' privately. An old example of how these sorts of systems work is presented in the video below,
Put simply; the applications are independant to where the data (of each user) is stored; and in-turn, the webizen ecosystem works are uplifting old works - to shift away from a model that was previously about 'knowledge banks' that supported human agency, given there was clearly no interest shown by the market in seeking to provide that sort of thing; towards a different model, which is about people owning their own robots - that i call - webizen...
There's alot about how this ecosystem works that is very different to others; and at the heart of it all, is a desire to support the human rights of persons, in all sorts of meaningful ways. Yet. In-order to support the means for people to have this sort of device, and thereby also make use of various different types of currencies (including those relating to our biosphere (ie: energy) and sociosphere); and, in-order to provide an environment that supports safety protocols, that in-turn need - overall - needs to be linked with an 'identity'; as is also required to ensure that the person who buys a webizen, owns the fundamental part of the webizen that relates to them - their own private database of their lives, in-effect.
So whilst there's many applications more broadly - the fundamental one of great importance is to provide a means through which natural persons in their private capacity may be furnished with the tools to be provided digital agency.
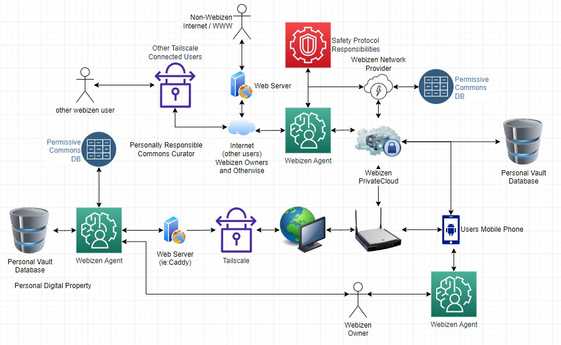
A basic diagram
In the diagram above, it illustrates the idea of a person having their own private database / vault, which is connected to / operating on various devices in their private networking environment; and that, the point being - they own their information. They can set-up their own online service or use one that is provided by a 'webizen alliance member'... therein also, is a seperate database system, that decentralises 'commons' information, that comes from various sources, has various stewards who have permissions in relation to the modification of those resources; but that, they're able to be distributed so that the local 'webizen agent' can process the information locally, without having to generate communications about what people are - in-effect - thinking about, all the time..
SO, the implication is that people effectively own their own private database that stores all the records about their lives - it is owned by them, and when they create electronic contracts with others to share and/or interact with others - that is managed via the permissive commons systems. It's ok if there's more than 1 person using a device attached to these systems because the private databases are independently stored to support that particular person. This means in-turn, that there needs to be a way to assign the ownership of that database (and related authentication / management instruments, etc.) to the owner of it.
Thereafter; how should these sorts of systems be provided to children, or how should permissions change if an elderly person is suffering from alzheimer's disease, or similar.
How should permissions be granted if a person becomes legally or medically incapable of managing their own affairs, or indeed - after death. How should carers for persons with severe disabilities be provided permissions to the lives of those persons.
- Should they be able to delete information? perhaps they abused the person, and they want no evidence.
- Should they be provided full and unfettered access to all of the information about that persons life? what if the access is sought via a false claim, as to instigate a wrongful attack.
- Should they be entitled to manage the financial affairs of that person? if so, how should disputes or oversight be supported?
- Should permission systems relating to parents - be set-aside; should the state become the guardian of all children, or should they simply be deemed an asset / property, like any other IoT device - of the mother of those children; and perhaps assign lawyers or social workers to adults - whilst i am not suggesting that this is the correct approach, it just seems like the sorts of approaches that are socially acceptable, other than simply leaving these issues to foreign authentication / data / AI providers like Google, Apple, Microsoft.
If these sorts of systems are developed - what Safety Protocols should be defined to protect the vulnerable? How do the vulnerable get access to justice? or is that only a feature that could be designed for the fortunate, those who are less likely to 'cause trouble', in-so-far as those who have suggested to be trusted as public officials might combatively suggest - rather than being able to point to the work that's been done to address these sorts of issues, because as they're 'doing it all already', those reports should be publically available - so that i wouldn't need to go about doing this work, to write about a problem that i cnanot find easily, a method to solve. Whilst my Top-Priority is to develop the first system to support the 'work app' that is in-turn intended to provide means to address the digital slavery issues, broadly,
In seeking to figure out the answer to this future problem; so that i can ensure the designs are equipped to provide a means to support persons other than capable adults; as independent human beings from a computing systems and artificial intelligence related Digital Identity perspective,
I reached-out to the DTA asking them about how the Identity Systems addressed the use-cases related to people who have some sort of guardianship related requirements, this was their response;
Thank you for contacting the Digital Transformation Agency (DTA).
Unfortunately, the DTA does not deal with guardianships, and therefore, cannot assist you with your enquiry.
We would suggest you to reach the Attorney-General’s Deparment:
Phone: (02) 6141 6666.
So - Dear Linkedin People - If you are able to point me towards any works that have been done about how to address the authentication and digital identity requirements associated with creating Electronic, AI related information storage, as is required to support personhood, human dignity / human rights, i would be thankful.
Note links to General AI Docs and in-turn also those relating to Tech Ethics. It is believed that the volume of use-cases that need to be made addressible, is a non-trivial amount of work; as such, i would expect the process to take some years before it is done well, if it is indeed the case that it hasn't really been done at all well - yet; As such,
I am presently unsure how these authentication systems should work; i am also unsure how they should be made able to be changed in a timely manner and what sorts of accountability systems should be applied in connection to any guardian related decisions made, in connection to the use and information held within that database.
Whilst the documentation is still developing, the link to the existing devDocs is here noting that there's much more to be done, particularly with respect to the permissive commons technology works - which are also instrumental. Yet, i do not like the idea of forging a semantic framework that might define persons other than legally capable adults; to be some form of property of others. There are all sorts of issues with that type of ideology, and i'm strongly apposed to it - perhaps the real answer today, is that it is better for vulnerable Australians to seek the support of our American friends, because the locals are reprobates.
idk. i hope not. furthermore, i note, these sorts of issues and opportunities are also meaningful for other regions around the world, so, whoever comes up with the best solution to the problem - i'm fairly sure those who care about loved-ones who may be positively impacted by good design, will be very thankful that someone did the work needed to help.
Follow-up article;
Is Chat GPT the most useful tool accessibly available to solve social problems? Here is a recent example.
In an article i wrote yesterday, i sought to express a desire to figure out how to address an underlying requirement for ecosystems that i'm developing that seek to support Human-Centric-AI and related informatics structures; noting, that it is well within the sphere of normal capacities of adults to enter into contracts that in-turn relate to the purchase of 'things' and therefore ownership of that thing, but for those who have guardianship related requirements, this is more difficult.
Here's a link to the Article; AI, Digital Identity & Guardianship Systems?
This has been an old problem - it is not new. Whilst the works i'm doing in an effort to address the far more broad nature of the underlying problems, is now being refactored; historically, the ability to get practically progressive solutions to address these sorts of problems, has been incredibly difficult. Only yesterday, was i chatting on linkedin with the Australian eSafety Commissioner (i think, could have been someone else using the account, idk); and whilst the account operator (which i think was likely Jullie - whose works i admire generally) provided the following response,

I soon thereafter recieved an email reply, per below.

Now, i'm not suggesting that there is a known connection between these two pieces of corraspondance. Frankly, the effect upon my line of enquiry, as is considered to be importantly considered - to address these very important considerations - has not led to any productively useful feedback or support.
That is - until i decided that i'd ask ChatGPT. Below is a copy of the statement, question and ChatGPT answer log that was produced just moments ago,
I have altered the sequence - by appending the list of affected persons at the top of this article - whereas it was originally the second last question i raised with it.
Q: make a list of the types of circumstances relating to a human being for whom these sorts of requirements are needed to support.
1. Children or young people who are not yet legally able to make decisions about their own personal and private information
2. Individuals with cognitive or developmental disabilities that impede their ability to make decisions about their own personal and private information
3. Elderly individuals who are experiencing cognitive decline or have diminished capacity to make decisions about their own personal and private information
4. Individuals with mental illness that affects their ability to make decisions about their own personal and private information
5. Individuals who are in emergency medical situations and unable to make decisions about their own personal and private information
6. Individuals who are incapacitated as a result of a physical or neurological injury or illness
7. Individuals who have a temporary or permanent loss of consciousness or brain function
8. Individuals who are in a state of extreme distress and unable to make decisions about their own personal and private information
9. Individuals who are under the care of a court-appointed guardian or conservator
10. Individuals who are in a long-term care facility or receiving in-home care.
11. Individuals who have suffered a traumatic event or have been victims of abuse, which may affect their ability to make decisions about their own personal and private information.
12. Individuals with addiction or substance abuse problems that impede their ability to make decisions about their own personal and private information.
13. Individuals who are in prison or detention centers, and may be limited in their ability to make decisions about their own personal and private information.
14. Individuals with a history of homelessness, or who are currently experiencing homelessness, and may have limited access to information management and technology.
15. Individuals who are living in remote or rural areas, and may have limited access to services and support that would help them manage their personal and private information.
It's important to note that, this list is not exhaustive and there may be other types of circumstances where support to manage personal and private information is needed, it's important to evaluate each situation and the needs of the person on a case by case basis.
It's important to keep in mind that individuals may experience temporary or permanent changes in their abilities and require different levels of support to manage their personal and private information. The key is to work with the individual and assess their specific needs to provide the appropriate level of support and to make sure that their human rights and autonomy are respected.
Now therefore; here is an illustration of the productivity benefits for doing good work to support human rights, AI Agents such as ChatGPT offers for people who are seeking to produce useful outcomes - without enough support or engagement by others otherwise. (to some degree, i wonder how government employees might in future be expected to at least use these sorts of agents to respond to enquiries in a manner that is better than is historically demonstrated?).
My Introductory Statement to ChatGPT:
I am working on software that supports entity logic.
In this design logic;
The term Entity Centric refers to legal entities, whether they be individual natural persons or legal persons (incorporated entities, government entities, etc.).
The terms Agent Centric and Agent refers to things that do stuff. A well known sub-class is Person, representing people. Other kinds of agents include Organizations, Groups, software and other 'things'. and,
The term Human Centric refers to the orientation of information management systems that centre upon the rights, responsibilities and moral ownership of electronic records pertaining to a human being.
Some Human Beings are not able to make legal decisions or hold legal responsibility on their own behalf. This may be due to disability, psychiatric illness, aging related conditions, emergency medical situations as well as consideration for the needs of children. This may be considered to relate to persons who have some sort of guardianship requirements to support the persons human rights.
If each Adult Human being is able to own, store and operate their own data / information and manage their own authentication and permissions systems, but that this cannot be achieved for persons who require some sort of guardianship support; how could systems be designed to support the safety and human dignity / human rights of persons who require guardianship related shared permissions structures and how could those permission structures be defined to support the persons human rights / human dignity?
Chat AI:
Designing systems that support the safety and human rights of individuals who require guardianship can be a complex task, as it involves balancing the need to protect the individual's rights and dignity with the need to ensure their safety. One approach to this problem is to use a combination of technical and policy-based solutions.
In terms of technical solutions, systems can be designed to support flexible permission structures that can be tailored to the specific needs of each individual. For example, the system could allow for different levels of access and control depending on the individual's needs and abilities. For example, individuals who require more support may have more limited access to their data, while those who are able to make decisions on their own may have more autonomy.
In terms of policy-based solutions, systems can be designed to incorporate principles such as transparency, accountability, and privacy by design. These principles can help ensure that the system is designed with the protection of the individual's rights and dignity in mind, and that any decisions or actions taken on their behalf are fully justified and transparent.
In addition, having clear protocols for guardianship and determining guardianship, and clear transparent communication channels for guardianship decision making would be essential. This can be achieved by having legal frameworks that clearly outline the responsibilities and rights of all parties involved, as well as regular reviews to ensure that the individual's needs are being met and that the guardianship is still needed.
Ultimately, it is important to involve individuals who require guardianship, their guardians and other stakeholders in the design process to ensure that the system is tailored to their specific needs and that it meets their safety, security and human rights standards.
My Question: if a person who requires guardianship is defined as a dependant; who still retains human rights, but is dependant upon one or more others to be supported to maintain a beneficial relationship with those rights; What technical designs could provide the dependent their own digital human agency, perhaps through the ownership of a database that contains their information; but is supported by others who also have access? how might the information be categorised to appropriately provide support, as well as maintaining the dependants right to privacy and freedom of thought?
ChatGPT:
One approach to providing a dependent with their own digital human agency, while also supporting them with access to their information, could be to use a decentralized database system. This type of system would allow the dependent to have control over their own data, while also allowing designated individuals, such as guardians, to have access to the data as needed.
The information in the database could be organized in such a way that it supports the dependent's needs and rights, while also protecting their privacy. For example, sensitive personal information could be kept private and only shared with designated individuals on a need-to-know basis. Information that is needed to support the dependent's daily needs could be more easily accessible by their guardians.
One way to organize the information to support the dependent is to use a hierarchical structure where personal data is separated into different levels of privacy and accessibility. For example, the dependent could have full control over the highest level of data, which includes information such as their medical history, contact information, and personal preferences. The lower level of data is shared with the designated guardians or support people and it can contain information such as appointments, social and other interactions that the dependant would have.
Another design solution could be to use a permission-based system, where the dependent and their guardians can assign different levels of access to the data for different individuals or groups. For example, the dependent may allow their primary guardian to have full access to all of their data, while other family members or caregivers may have more limited access. Additionally, consider setting up expiration dates for access, so that the data is not indefinitely accessible.
To maintain the dependent's right to privacy and freedom of thought, it is also important to have clear policies and procedures in place for handling data, as well as regular audits to ensure that the system is in compliance with regulations, standards and to assure dependant's information is being handled appropriately. Additionally, involving the dependant in the decision making process and choices of the systems, protocols and policies that would be employed to support their human agency can help ensure that their needs and rights are being met.
Another important aspect of maintaining the dependent's right to privacy and freedom of thought is to provide them with the necessary tools and resources to understand and manage their own data. This could include providing training and education on how to use the database and permission system, as well as giving them access to clear and easy-to-understand information about their rights and the policies and procedures that apply to their data.
Additionally, involving the dependent in the decision-making process when it comes to the use of their data, can be essential. For example, they can have a voice in which of the data they allow to be shared with which parties, and under what conditions.
Finally, it is important to have robust security measures in place to protect the dependent's data from unauthorized access or misuse. This can include using encryption, secure authentication methods, and regular backups to protect the data from loss or damage.
In summary, providing a dependent with their own digital human agency can be achieved through the use of decentralized databases and permission-based systems that allow the dependent to have control over their own data, while also allowing designated individuals to have access as needed. The system should be designed to support the dependent's needs and rights, while also protecting their privacy, including through the use of hierarchical data structure, expiration date of access, and involving the dependant in the decision making process of sharing and managing the data. To maintain dependant's rights, security measures must be in place, as well as clear policies and procedures for handling the data, regular audits and involving dependant in the decision making process.
My Question: What sorts of policy based mechanisms would be required and/or beneficial to support the human rights of the dependant?
ChatGPT:
There are a variety of policy-based mechanisms that can be implemented to support the human rights of a dependent. Some of these include:
1. Clear legal frameworks: Establishing clear legal frameworks that outline the rights and responsibilities of all parties involved in supporting the dependent, including their guardians, caregivers, and family members. These frameworks should also provide guidelines for decision making and dispute resolution.
2. Human rights-based approach: Ensuring that the approach taken to support the dependent is based on the principles of human rights, including the right to autonomy, privacy, and dignity. This should include regular reviews of the dependent's needs and the effectiveness of the support being provided, to ensure that their rights are being respected.
3. Transparency and accountability: Implementing systems and procedures that promote transparency and accountability in the handling of the dependent's data and in the decision-making process around their care. This can include regular reporting, regular audits, and mechanisms for addressing grievances.
4. Privacy and security: Developing and implementing policies and procedures that protect the dependent's privacy and personal information, including strict protocols for data handling, regular security reviews, and the use of encryption, authentication and access control mechanisms.
5. Participation and informed consent: Involving the dependent in the decision-making process, providing them with the information necessary to understand the choices being made, and ensuring that they are able to provide informed consent.
6. Independent oversight: Having independent oversight and regular review mechanisms to ensure that the dependent's rights are being respected and protected, and to identify and address any concerns or issues that may arise.
7. Monitoring: Establishing regular monitoring, reporting and review mechanisms to ensure compliance with the above mentioned policy based mechanisms and identify and addressing any issues.
It is important to note that, depending on the specific context and needs of the dependent, additional policy mechanisms may be necessary to ensure their human rights are protected.
My Question: If a dependant is unable to independently own or lawfully protect (ie: via courts of law) their own rights relating the ownership, storage and use of their own personal and private information; how might a legal structure be devised to support their needs, with the support of others?
ChatGPT:
If a dependent is unable to independently own or lawfully protect their own rights relating to the ownership, storage, and use of their personal and private information, a legal structure could be devised to support their needs with the support of others.
One approach could be to establish a legal guardianship or conservatorship system. This would involve a legal process where a designated guardian or conservator is appointed by a court to make decisions on the dependent's behalf regarding their personal and private information. The guardian or conservator would be responsible for managing the dependent's data and ensuring that their rights and interests are protected.
Another approach could be to establish a legal trust, where the dependent's data would be held in trust by a designated trustee. The trustee would be responsible for managing and protecting the dependent's data, in accordance with the terms of the trust and any court orders. This legal trust can be tailored to the specific needs of the dependant and the level of autonomy they wish to retain.
The legal structure that is chosen would need to be in compliance with the local jurisdiction laws, while also taking into account of the needs and autonomy of the dependent person. Additionally, it would need to be reviewed and updated on regular basis.
In both cases, the legal structure would need to provide for oversight and accountability to ensure that the dependent's rights and interests are protected, and to address any issues or concerns that may arise. This could be through regular reporting, regular reviews, or mechanisms for dispute resolution, as appropriate.
It is also important to consider involving a range of stakeholders in the design and implementation of such legal structures, such as the dependant, their guardians, family members and other support people. This will help ensure that the legal structure meets the specific needs of the dependent, respects their autonomy and rights, and is tailored to the dependant's individual needs and circumstances.
Another approach to support the needs of dependants with the support of others could be by creating a power of attorney (POA). A power of attorney is a legal document that gives someone else the authority to make decisions on behalf of the person who has granted the POA. This could be a general POA which gives someone the authority to make all types of decisions, or a specific POA which gives someone the authority to make specific types of decisions related to personal and private information. In this case, the person granting the POA (the principal) would have the right to choose who their attorney-in-fact (the person they have chosen to act on their behalf) will be, and what kind of power they will have. The attorney-in-fact should act in the best interest of the principal, and in this case of the dependent, the attorney-in-fact would manage the dependent's personal and private information according to the terms of the POA and the best interest of the dependent.
Another potential legal solution that might support dependants and their rights over their personal and private information, could be the creation of a legal representative. This could be a person, or an organization that is legally designated to represent the dependent in the management and protection of their personal and private information. This legal representative would be responsible for making decisions related to the dependent's information, such as sharing it with others or managing the privacy settings, and would act in the best interest of the dependent, while also complying with legal requirements.
It is also important to mention that, any solution that is chosen, it should not limit or restrict the dependent's rights more than is necessary to protect their best interests and they should be included in the decision making process and have the right to revoke the legal structure if they choose to do so.
In summary, there are a number of legal structures that can be devised to support the needs of dependants with the support of others, such as legal guardianship or conservatorship, legal trust, power of attorney, and legal representative. The specific legal structure chosen will depend on the jurisdiction and the specific needs and circumstances of the dependent. It is important to note that, regardless of the legal structure chosen, it should prioritize the dependent's autonomy and rights while also ensuring they are protected and their best interest is taken into account.
My Question: How could a solution that attends to the considerations provided earlier; be devised using contract law between private individuals, that may in-turn expire as a consequence of some sort of condition having been met?
ChatGPT:
It is possible to devise a solution using contract law between private individuals that attends to the considerations provided earlier and that may expire as a consequence of some sort of condition having been met. One example of such a contract could be a personal data management contract.
This type of contract would outline the terms and conditions of how the dependent's personal and private information will be managed and protected. The contract would be between the dependent (or the person legally responsible for them) and the person or organization designated to manage their data, such as a guardian, attorney-in-fact, or legal representative. The contract would include information such as the scope of the data that is being managed, the rights and responsibilities of each party, and the conditions under which the contract may be terminated or modified.
The contract could include an expiration clause, which would specify a certain condition or set of conditions that, when met, would result in the contract coming to an end. For example, the contract could expire when the dependent reaches a certain age or when their condition improves to a point where they are able to manage their data independently.
In addition, the contract should include provisions for regular reviews of the terms and conditions of the contract to ensure that it is still meeting the needs of the dependent and that their rights are being protected. It should also include provisions for dispute resolution, in case of any disagreement about the contract's terms or the management of the data.
It is important to note that any contract involving personal data should comply with relevant data protection laws, privacy laws and human rights laws, and that the dependent should be involved in the contract creation, review and termination process.
In summary, a solution that attends to the considerations provided earlier could be devised using contract law between private individuals. This contract, such as a personal data management contract, would outline the terms and conditions of how the dependent's personal and private information will be managed and protected and includes an expiration clause that specifies a certain condition or set of conditions that, when met, would result in the contract coming to an end. It should also include provisions for regular reviews and dispute resolution and comply with relevant data protection laws, privacy laws and human rights laws.
Another important aspect of this type of contract would be its enforceability. It's important to make sure that the contract is legally binding and that the rights and obligations of the parties are clearly defined and enforceable in court if needed. This can be done by including specific language in the contract that makes it clear that it is intended to be legally binding and that the parties have read and understood the terms of the contract before signing.
Additionally, it would be beneficial to consider involving legal professionals in the drafting and review of the contract, to ensure that it meets the legal requirements and that it's terms are fair and reasonable to all parties involved.
It's also worth noting that, in some cases the contract could be used in parallel with or as part of a legal framework that is established by the government such as a guardianship or conservatorship structure, or a legal trust. In this case, the contract would need to be aligned with and comply with the legal framework that is in place.
In summary, a solution that attends to the considerations provided earlier could be devised using contract law between private individuals, that may in-turn expire as a consequence of some sort of condition having been met. This type of contract, would provide clear and enforceable terms and conditions for the management and protection of the dependent's personal and private information, and would include an expiration clause that specifies a certain condition or set of conditions that, when met, would result in the contract coming to an end. It should be legally binding and comply with relevant data protection laws, privacy laws and human rights laws. It's recommended to involve legal professionals in the drafting and review of the contract, to ensure that it meets the legal requirements and it's terms are fair and reasonable for all parties involved.
My Question: make a list of the types of circumstances relating to a human being for whom these sorts of requirements are needed to support.
1. Children or young people who are not yet legally able to make decisions about their own personal and private information
2. Individuals with cognitive or developmental disabilities that impede their ability to make decisions about their own personal and private information
3. Elderly individuals who are experiencing cognitive decline or have diminished capacity to make decisions about their own personal and private information
4. Individuals with mental illness that affects their ability to make decisions about their own personal and private information
5. Individuals who are in emergency medical situations and unable to make decisions about their own personal and private information
6. Individuals who are incapacitated as a result of a physical or neurological injury or illness
7. Individuals who have a temporary or permanent loss of consciousness or brain function
8. Individuals who are in a state of extreme distress and unable to make decisions about their own personal and private information
9. Individuals who are under the care of a court-appointed guardian or conservator
10. Individuals who are in a long-term care facility or receiving in-home care.
11. Individuals who have suffered a traumatic event or have been victims of abuse, which may affect their ability to make decisions about their own personal and private information.
12. Individuals with addiction or substance abuse problems that impede their ability to make decisions about their own personal and private information.
13. Individuals who are in prison or detention centers, and may be limited in their ability to make decisions about their own personal and private information.
14. Individuals with a history of homelessness, or who are currently experiencing homelessness, and may have limited access to information management and technology.
15. Individuals who are living in remote or rural areas, and may have limited access to services and support that would help them manage their personal and private information.
It's important to note that, this list is not exhaustive and there may be other types of circumstances where support to manage personal and private information is needed, it's important to evaluate each situation and the needs of the person on a case by case basis.
It's important to keep in mind that individuals may experience temporary or permanent changes in their abilities and require different levels of support to manage their personal and private information. The key is to work with the individual and assess their specific needs to provide the appropriate level of support and to make sure that their human rights and autonomy are respected.
My Question: please define an ontology using RDF, RDFS, OWL SKOS, SOIC and SHACL that illustrates an example of how this might work.
An ontology using RDF, RDFS, OWL, SKOS, SHACL and SOIC to illustrate an example of how this might work would be a complex task, as it would involve several steps, such as identifying the classes, properties, and relationships in the domain, defining the concepts and their hierarchies, and specifying the constraints and rules that govern the data.
However, I can provide an overview of how such an ontology might be structured, and some examples of the types of classes, properties, and relationships that would be used to represent the domain.
- RDF (Resource Description Framework) would be used to define the basic structure of the ontology, providing a way to represent resources and the relationships between them.
- RDFS (RDF Schema) would be used to define classes and properties, and to provide a way to specify the hierarchical relationships between classes and properties.
- OWL (Web Ontology Language) would be used to provide more advanced modeling features, such as expressing cardinality and property restrictions, and defining classes and properties as equivalent or disjoint.
- SKOS (Simple Knowledge Organization System) would be used to express concepts and their relationships, and to provide a way to organize and browse the concepts in the ontology.
- SHACL (Shapes Constraint Language) would be used to specify constraints and rules that govern the data, such as data types, cardinality, and allowed values.
- SOIC (Supporting Open Identity & Control) would be used to express information related to the human identity, their rights, and access management.
As an example, the ontology might include classes such as "Dependent", "Guardian" and "Data Manager", where "Dependent" would be a subclass of "Person" and "Guardian" and "Data Manager" would be subclasses of "Agent". The classes would be related through properties such as "hasGuardian" and "hasDataManager" where the properties would be defined as object properties linking "Dependent" with "Guardian" and "Data Manager" respectively. The ontology would also include classes such as "Personal Information" and "Privacy Rights" which would be related through properties such as "hasPersonalInformation" and "hasPrivacyRights" where the properties would be defined as object properties linking "Dependent" with "Personal Information" and "Privacy Rights" respectively. The ontology might also include properties such as "accessLevel" and "permission" which would be defined as data properties linking "Dependent" with "Personal Information" and "Privacy Rights" respectively, to indicate the level of access and permission granted to the different parties involved.
The ontology would also include a class "Data Management Contract" which would be related to "Dependent", "Guardian", "Data Manager" and "Personal Information" through properties such as "hasContract", "hasDependent", "hasGuardian", "hasDataManager" and "hasPersonalInformation" to indicate the parties involved and the terms and conditions of the contract.
In addition, the ontology could also include classes such as "Data Protection Law", "Privacy Law" and "Human Rights Law" that would be related through properties such as "compliesWith" linking "Data Management Contract" with "Data Protection Law", "Privacy Law" and "Human Rights Law" respectively to indicate the laws that the contract must comply with.
It's important to note that this is a high level example and the details of the ontology would have to be fleshed out further, with a more detailed understanding of the domain and specific requirements. Also, the use of different vocabularies and ontologies, it is important to ensure that the ontology is consistent and coherent and that the different vocabularies and ontologies are used in a way that is consistent with their intended purpose. In addition, it is important to use established vocabularies and ontologies when they are available, to make sure that the ontology is compatible with other ontologies and can be integrated with other systems.
Furthermore, one important aspect of the ontology is to make it flexible, to allow for future changes and extensions. It should be easy to update, to add new classes, properties and relationships, and to change the existing definitions as new information is acquired.
In summary, an ontology using RDF, RDFS, OWL, SKOS, SHACL and SOIC to illustrate an example of how the support for dependants over their personal and private information might work, would involve several steps and could make use of different vocabularies and ontologies to create a coherent and consistent model that represents the domain, while also being flexible enough to allow for future updates and extensions. The ontology would need to include classes and properties that represent the different parties involved, the personal and private information, the contract and the laws. It should also include relationships that express the connections between these different components, and constraints that ensure data accuracy and consistency, while also complying with the legal requirements.
My Question: write a prompt for DALL·E 2 that will provide a diagram that describes this sort of systems component.
"Please create a diagram that illustrates the different components and relationships of a system that supports the management and protection of personal and private information for dependents, including classes such as "Dependent", "Guardian", "Data Manager", "Personal Information", "Privacy Rights", "Data Management Contract", "Data Protection Law", "Privacy Law" and "Human Rights Law". The diagram should show the relationships between these classes, such as the "hasGuardian" and "hasDataManager" properties linking "Dependent" with "Guardian" and "Data Manager" respectively, and the "compliesWith" property linking "Data Management Contract" with "Data Protection Law", "Privacy Law" and "Human Rights Law" . Show also how constraints and access management are enforced through the system."

(ok, so sadly, - it didn't seem to produce anything really useful that way, yet.)M
Now, for what its worth (FWIW) - the actual mechanisms i'm looking to employ to support the semantically empowered permissions systems of a Webizen AI Agent; are actually, far more complex than the relatively simple context that i've asked ChatGPT to comment on; yet, the underlying methodologies to support some sort of way for persons other than legally capable and independent adults to be technically furnished with some methodology that is designed to support the human rights of those persons - well, i think i was able to figure out the basics well enough, not through my efforts to seek other human beings to help me figure out how to achieve these sorts of outcomes for those whom are impacted by technology who are members of these classes or circumstances relating to natural persons; not simply for the purpose of the Webizen related works alone, but more broadly as a matter of importance in relation to the practice of Web Civics and related Peace Infrastructure Project works. If you'd like to get involved, not that i've set-up a LinkedIn group for the Peace Infrastructure Project, and whilst its still early days - i think, i've made enough useful progress in my efforts to address this issue - that i'm now able to move forward with defining how the entity structures for managing information via these Human Centric information structures - can now therefore be made able to work.
Perhaps also - as is somewhat central to the underlying implications; the use of ChatGPT to successfully better define some context for how a solution might be designed to address these sorts of problems, whilst it is not entirely solved / complete; and is likely to contain some errors and/or related issues,
The productivity and therefore also - if caculated in terms of the expenditure of energy - to achieve some sort of goal, level of progress or outcome; is certainly demonstrating the benefits of ChatGPT to address SDG related issues in a manner that will Ontologically (ie: a SDG Ontology example) provide performance benefits that far exceed what has otherwise been demonstrated.
Now,
I need to get back to the work required to produce the design documentation for the rest of the ecosystem - as to ensure, i've covered the main topics prior to getting stuck into developing the software for the first usable version, that is thereafter able to be further developed to support the needs of others, irraspective of their circumstances - so long as they care about the human rights of both themselves and others.
Whilst ChatGPT may not be able to write or define via art, the sorts of things that we consider to be part of our Australian Way,
The Australian Way from AusCivics on Vimeo.
There is no question about whether or not these sorts of tools can be used to support the material realisation of those sorts of values, in a manner that can become part of the experience of what it means, to be Australian; or more broadly, Human. When seeking input to address issues that relates to human rights - that perhaps, too many people do not understand?
It has been my experience, that the use of ChatGPT is revolutionising the means for people to do useful work in areas that they'd otherwise be discouraged to progress. The greatest threat presented by AI, isn't about the 'AI things' themselves, its the behaviour of human beings - that will make all the difference.